Wency Lum, the AVP at UVIC’s IT department recently gave a talk on cybersecurity and how it relates to us taking Digital Literacy (EDCI136)- and I wanted to share the points I found the most interesting.
The importance of cybersecurity
Lum starts her presentation by covering a few ways that cybersecurity should integrally be practiced, when going online as a student:
As a digital citizen and student, you should practice:
- digital ID/data protection
- Awareness of new threats, and resilience against them
- Responsible online behaviour
Why cybersecurity’s a big deal
Cybersecurity, as Lum goes on to explain, is an area of work that doesn’t have enough experts in the field. Cybercriminals are getting increasingly harder to catch, because they can hide behind a digital identity, investigators have no in-person crime to be found. The medical sector for example, has become a significant target for cybercrime, since a lot of their systems are often outdated, and those on the receiving end come unprepared for an attack or how to handle it. Last year, UnitedHealthcare (an American health insurance company) was hit with a ransomware attack, grinding medical services they operated to a ten-day halt.
Their then-CEO reported that the company paid 22 million USD in ransom to free the records they had stolen from them. UnitedHealthcare has also been estimated to be spending 2.3. billion dollars to recover and develop response to cyberattacks.
The other fact that’s important is the fact that they paid the ransom, and it’s public that they paid the ransom– and it ends up highlighting that attacking healthcare is profitable. And that’s really important because when a sector becomes vulnerable like that, it will be subject to more attacks. And that’s how the attackers operate; they find a sector that’s lucrative and they attack it over and over again, and then they find new victims.
Wency Lum, AVP of IT at UVIC
Another example that Wency Lum highlights was an update to Crowdstrike’s security software that happened in the summer of 2024, that accidentally bluescreened countless Windows computers worldwide- and that was a big deal because Windows has become the default operating system across almost every major sector on Earth. Airports, corporations and even Formula 1 teams were all affected by the outage until it was finally fixed using great efforts and expense.
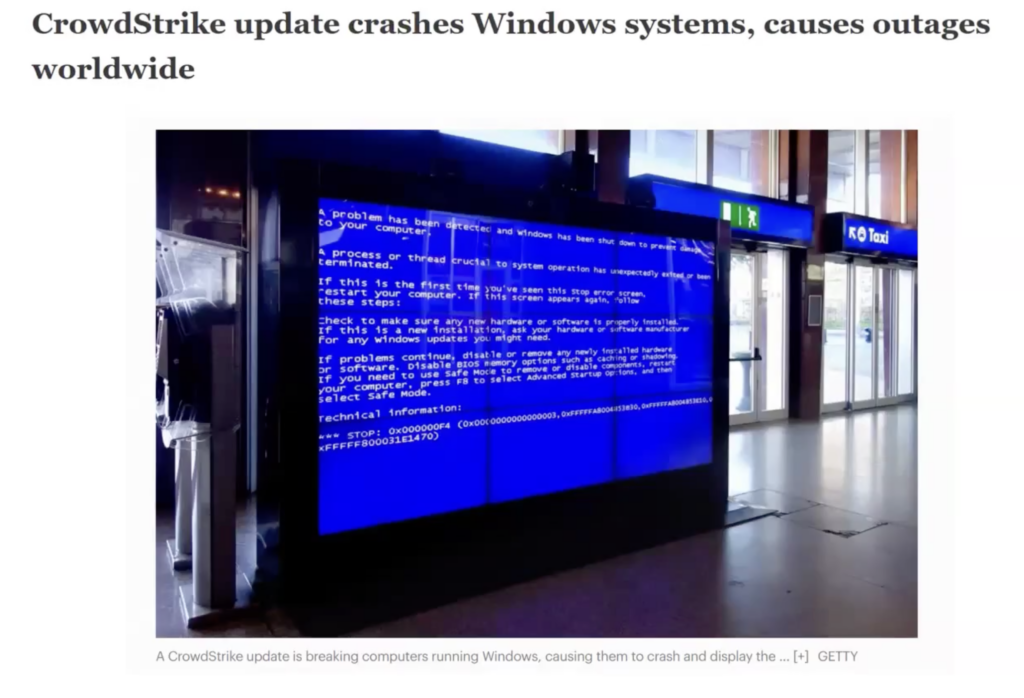
Which leads us to why cybercrime has become popular in the first place; it’s low-cost (as the needed services can easily be bought on the dark web) and enables attackers to perform crime like robberies with zero in-person contact with their target. Catching and prosecuting the perpetrators behind a cyberattack can be almost impossible since there’s little physical evidence left behind, and not enough experts in the field who can properly understand it. Cybercrime this year alone is expected to cost 10.5 trillion dollars, more than all drug trafficking combined– and it’s a sector that’s full of young talent, too. The average cybercriminal is about 19 years old, whereas the average in-person criminal was 18 years older.

This means that we’ll need newer, more advanced ways of categorizing cybercrime to better understand it. After three years of hard research, Oxford University recently came up with a chart, indicating the country of origin of major cyberattacks. Russia, China and Ukraine rounded out the top three. This isn’t perfectly accurate, though.

Lots of cyberattacks come from addresses that are spoofed, pretending to be from another country that isn’t their real home- and the chart doesn’t take state sponsored attackers into account- which is when governments either hire organized crime groups to proxy their work or IT officials under their government umbrella.
There are people’s jobs in IT where you may actually be hacking- that sounds crazy to us, but in certain countries they will outsource hacking to the mafia or organized crime because it’s a source of revenue for them.
WEncy lum
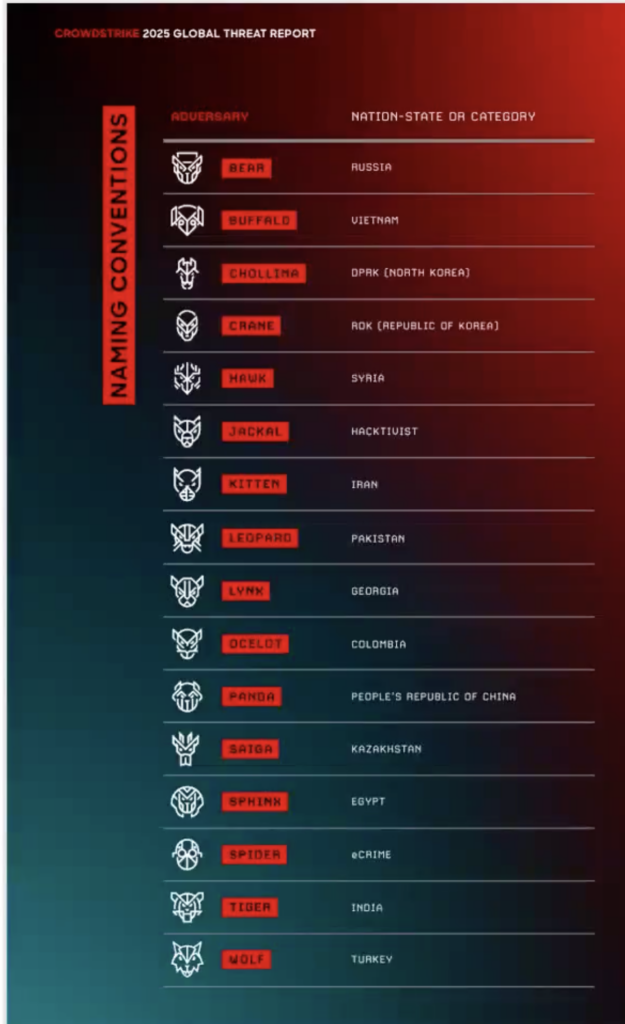
To classify state sponsored hacking groups, Crowdstrike (the group from earlier that accidentally took the world’s Windows machines offline) came up with a codenaming scheme that ties a country’s groups to an animal commonly found in that country’s national stereotypes. Using Crowdstrike’s codenames, Russian groups are given the suffix Bear, Chinese groups Panda, and so on. The only rare exceptions to this rule are for Kazakstan (named Saiga), North Korean groups (named Chollima- 천리마, after a winged horse in Asian mythology,) and lastly dark web operations, given the nickname Spider.
What to look for in cyberattacks
The quickest way in for the vast majority of cyberattacks is human error. These could include poor security or passwords (bonus points if they’re reused, enabling attackers access to multiple accounts), ransomware, or social engineering attacks and phishing- all of which rely on the victim on the receiving end to reveal an open loophole themselves.
As the damage caused by cyberattacks gets bigger, so does their complexity. As Lum explains, cybercrime is a proven and repeatable formula that can massively increase in size, frequency and intensity. A traditional bank robbery could take months of planning before it’s executed, whilst a cybercriminal could hit hundreds of them overnight with just the right phishing email. And as GenAI (generative AI chatbots) have become more mainstream, attackers are taking full advantage of it to speed up attacks even further. GenAI is incredibly good at gathering data en masse in a short amount of time, and they can be easily customized to suit the type of attacking needed. Chatbots are also currently being used to create fake social media profiles, or even write phishing emails that are a lot more convincing than say, running an ‘urgent message to the CEO’ telling them to open a PDF in Ukrainian through a translator.
This is already in practice by Famous Chollima, a North Korean group that used GenAI to whip up fake LinkedIn profiles. Social engineering schemes can also directly target AI models by feeding them misinformation- turning them into adversarial models confused by their incoming data.

How to improve your personal cybersecurity, for students

UVIC students personally get hit by phishing emails all the time, and if you want to see some genuine examples of the emails they receive, I suggest you check out the UVIC Phish Bowl.
A few of the common symptoms you’ll find on phishing emails include:
- A false sense of urgency, or promise. A common one amongst UVIC students is a fake notice that would in theory require them to start a part-time job, when they’re actually asking you for banking information to flood your account with purchases and eventually debt.
- Check if the email is actually a screenshot. This is a tactic used to get past spam filtration systems, making them seem more legit.
- Spelling mistakes. Watch for an inconsistent, or awkward tone, this is usually a dead giveaway. This is getting harder to spot now that chatbots are being used as a ghostwriter to make the emails sound more human.
- Are they asking for your personal information? Phishing emails sent to UVIC students will consistently ask them for their personal email address and banking information to take them off the UVIC network, and thus monopolizing intel away from the IT department. These emails are usually sent from Gmail accounts, but they can spoof UVIC addresses, too- keep your eyes peeled for an address that doesn’t match the sender’s name.
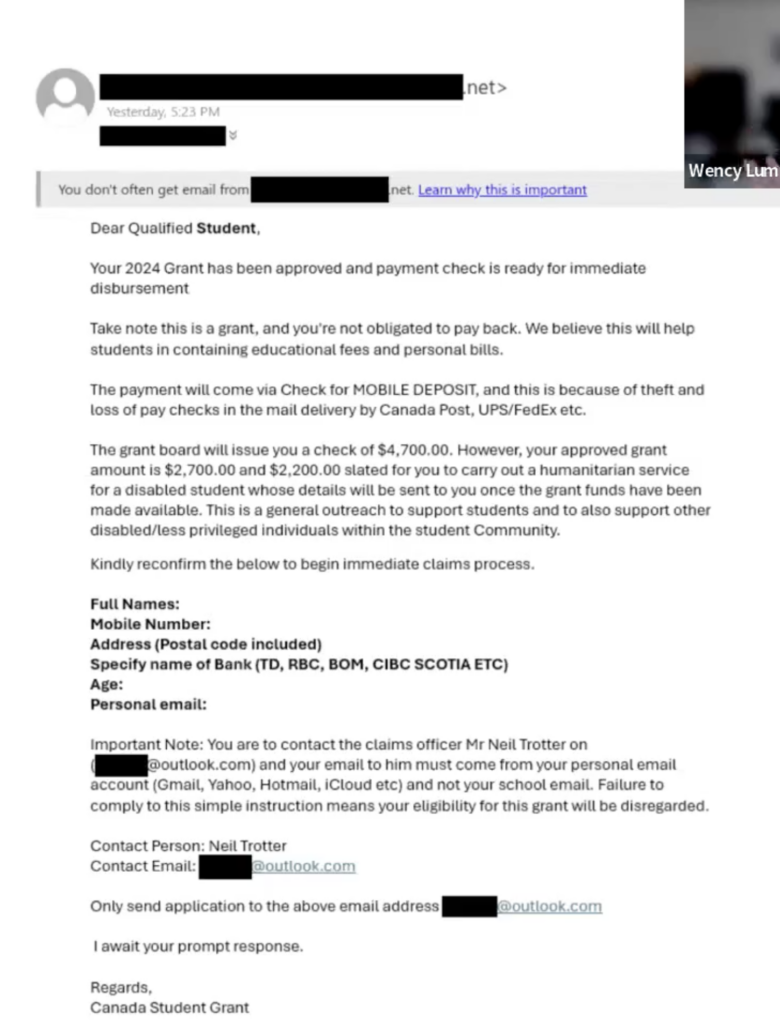
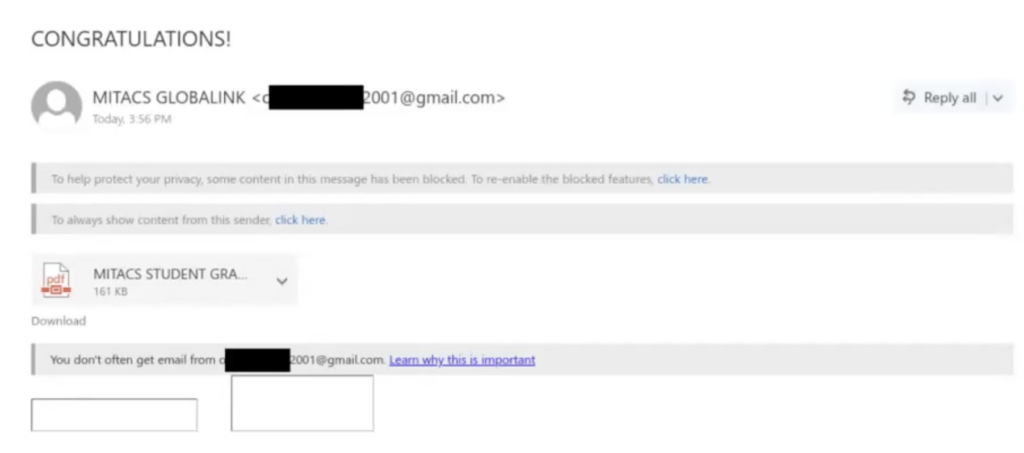
a few examples of emails that hit real UVIC students in the past.
This leads us to the ultimate question surrounding cybersecurity: what can we do? We can start by covering up weak points in our online security. We can start with the obvious points like not reusing or sharing passwords, which can be further improved using MFA (that’s multi-factor authentication, which is already required to be used by everyone at UVIC), and avoiding pirated software, if possible. I remember I used to download them a lot when I was a desperate, seven-year old Minecraft player when the game was at its peak in popularity. Flat out refusing to pay for mods to the game, I tried downloading cracked versions that ultimately led to my computer being flooded with bloatware. At the time, I had no concept of making my own money, and was willing to fork over my entire online presence in exchange for a piece of software- which is exactly the type of people these websites aim to infect.
In other words, stay calm, stay vigilant, and update your passwords and security measures to keep up with the times. Wency Lum hosted an incredible guest lecture packed with information relevant to this course, and I expect nothing less from a woman holding such a senior position in IT.
Leave a Reply